Prepare for Fortinet NSE8 exam with latest Fortinet NSE NSE8 dumps pdf training resources and study guides free try. Fortinet NSE NSE8 dumps exam preparation kit contains all the necessary NSE8 questions that you need to know. “Fortinet Network Security Expert 8 Written (800)” is the name of Fortinet NSE https://www.leads4pass.com/nse8.html exam dumps which covers all the knowledge points of the real Fortinet exam. Get your Fortinet NSE NSE8 exam preparation questions in form of NSE8 PDF. 100% passing guarantee and full refund in case of failure.
Download free latest Fortinet NSE8 dumps pdf resources: https://drive.google.com/open?id=0B_7qiYkH83VRTWF6LWxYekxZYUE
Download free latest Fortinet NSE7 dumps pdf resources: https://drive.google.com/open?id=0B_7qiYkH83VRXzY4MVVCWHRQc1k
Useful Fortinet NSE NSE8 Dumps Exam Practice Questions And Answers (Q1-Q20)
QUESTION 1
The dashboard widget indicates that FortiGuard Web Filtering is not reachable. However, AntiVirus, IPS, and Application Control have no problems as shown in the exhibit.
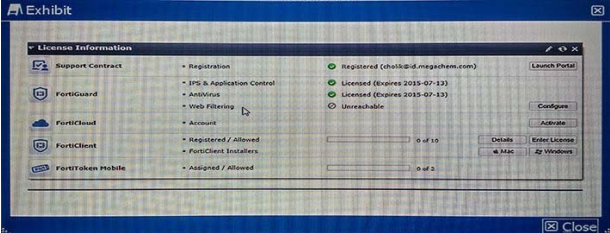
You contacted Fortinet’s customer service and discovered that your FortiGuard Web Filtering contract is still valid for several months.
What are two reasons for this problem? (Choose two.)
A. You have another security device in front of FortiGate blocking ports 8888 and 53.
B. FortiGuard Web Filtering is not enabled in any firewall policy.
C. You did not enable Web Filtering cache under Web Filtering and E-mail Filtering Options.
D. You have a firewall policy blocking ports 8888 and 53.
Correct Answer: BD
QUESTION 2
A customer is authenticating users using a FortiGate and an external LDAP server. The LDAP user, John Smith, cannot authenticate. The administrator runs the debug command diagnose debug application fnbamd 255 while John Smith attempts the authentication:
Based on the output shown in the exhibit, what is causing the problem?
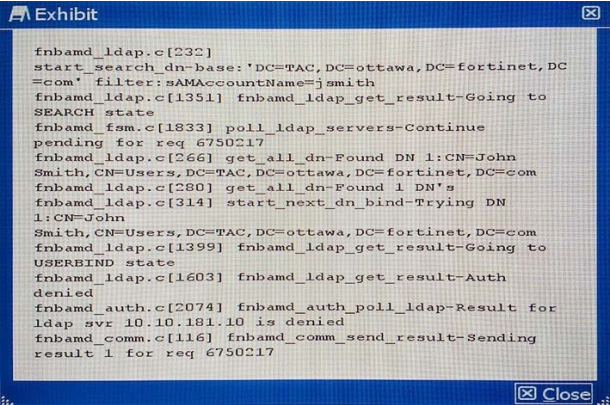
A. The LDAP administrator password in the FortiGate configuration is incorrect.
B. The user, John Smith, does have an account in the LDAP server.
C. The user, John Smith, does not belong to any allowed user group.
D. The user, John Smith, is using an incorrect password.
Correct Answer: A
QUESTION 3
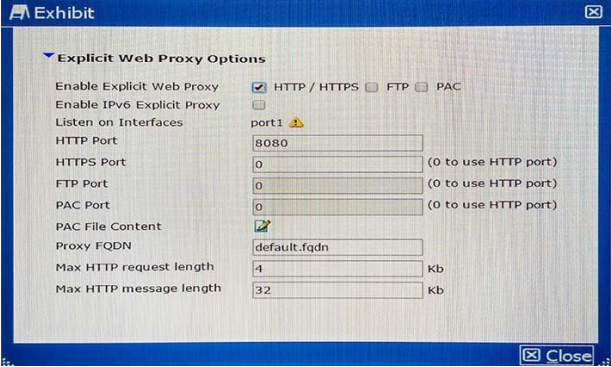
The exhibit shows an explicit Web proxy configuration in a FortiGate device. The FortiGate is installed between a client with the IP address 172.16.10.4 and a Web server using port 80 with the IP address 10.10.3.4. The client Web browser is properly sending HTTP traffic to the FortiGate Web proxy IP address 172.16.10.254.
Which two sniffer commands will capture this HTTP traffic? (Choose two.)
A. diagnose sniffer packet any `host 172.16.10.4 and host 172.16.10.254′ 3
B. diagnose sniffer packet any `host 172.16.10.254 and host 10.10.3.4′ 3
C. diagnose sniffer packet any `host 172.16.10.4 and port 8080′ 3
D. diagnose sniffer packet any `host 172.16.10.4 and host 10.10.3.4′ 3
Correct Answer: CD
QUESTION 4
Your colleague has enabled virtual clustering to load balance traffic between the cluster units. You notice that all traffic is currently directed to a single FortiGate unit. Your colleague has applied the configuration shown in the exhibit.
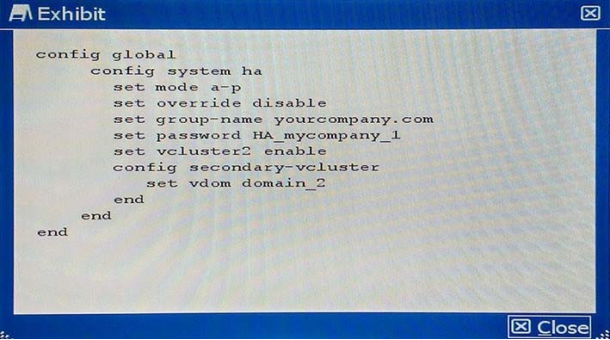
Which step would you perform to load balance traffic within the virtual cluster?
A. Issue the diagnose sys ha reset-uptime command on the unit that is currently processing traffic to enable load balancing.
B. Add an additional virtual cluster high-availability link to enable cluster load balancing.
C. Input Virtual Cluster domain 1 and Virtual Cluster domain 2 device priorities for each cluster unit.
D. Use the set override enable command on both units to allow the secondary unit to load balance traffic.
Correct Answer: C
QUESTION 5
A data center for example.com hosts several separate Web applications. Users authenticate with all of them by providing their Active Directory (AD) login credentials. You do not have access to Example, Inc.’s AD server. Your solution must do the following:
– provide single sign-on (SSO) for all protected Web applications
– prevent login brute forcing
– scan FTPS connections to the Web servers for exploits
– scan Webmail for OWASP Top 10 vulnerabilities such as session cookie hijacking, XSS, and SQL injection attacks
Which solution meets these requirements?
A. Apply FortiGate deep inspection to FTPS. It must forward FTPS, HTTP, and HTTPS to FortiWeb. Configure FortiWeb to query the AD server, and apply SSO for Web requests. FortiWeb must forward FTPS directly to the Web servers without inspection, but proxy HTTP/HTTPS and block Web attacks.
B. Deploy FortiDDos to block brute force attacks. Configure FortiGate to forward only FTPS, HTTP, and HTTPS to FortiWeb. Configure FortiWeb to query the AD server, and apply SSO for Web requests. Also configure it to scan FTPS and Web traffic, then forward allowed traffic to the Web servers.
C. Use FortiGate to authenticate and proxy HTTP/HTTPS; to verify credentials, FortiGate queries the AD server. Also configure FortiGate to scan FTPS before forwarding, and to mitigate SYN floods. Configure FortiWeb to block Web attacks.
D. Install FSSO Agent on servers. Configure FortiGate to inspect FTPS. FortiGate will forward FTPS, HTTP, and HTTPS to FortiWeb. FortiWeb must block Web attacks, then forward all traffic to the Web servers.
Correct Answer: D
QUESTION 6
A company wants to protect against Denial of Service attacks and has launched a new project. They want to block the attacks that go above a certain threshold and for some others they are just trying to get a baseline of activity for those types of attacks so they are letting the traffic pass through without action. NSE8 dumps Given the following:
– The interface to the Internet is on WAN1.
– There is no requirement to specify which addresses are being protected or protected from.
– The protection is to extend to all services.
– The tcp_syn_flood attacks are to be recorded and blocked.
– The udp_flood attacks are to be recorded but not blocked.
– The tcp_syn_flood attack’s threshold is to be changed from the default to 1000.
The exhibit shows the current DoS-policy.
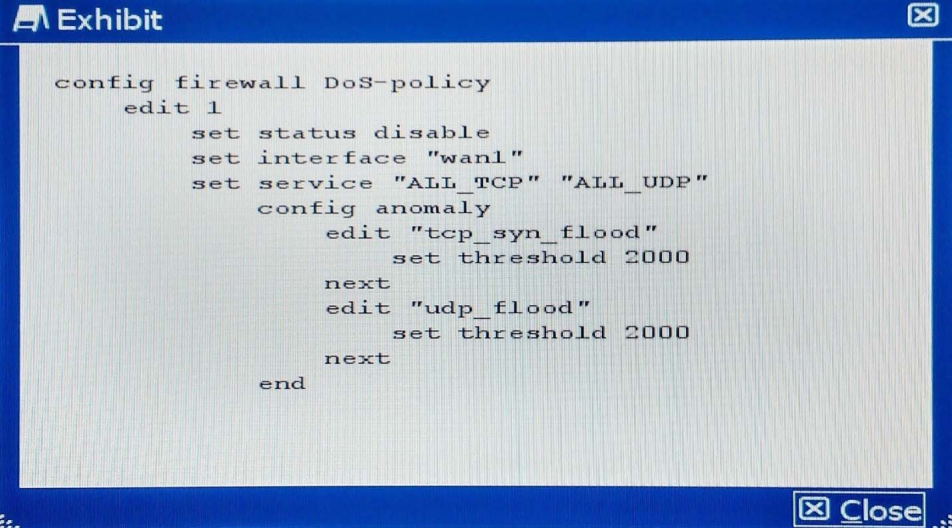
Which policy will implement the project requirements?


Correct Answer: BD
QUESTION 7
Your security department has requested that you implement the OpenSSL.TLS.Heartbeat.Information.Disclosure signature using an IPS sensor to scan traffic destined to the FortiGate. You must log all packets that attempt to exploit this vulnerability. Referring to the exhibit, which two configurations are required to accomplish this task? (Choose two.)
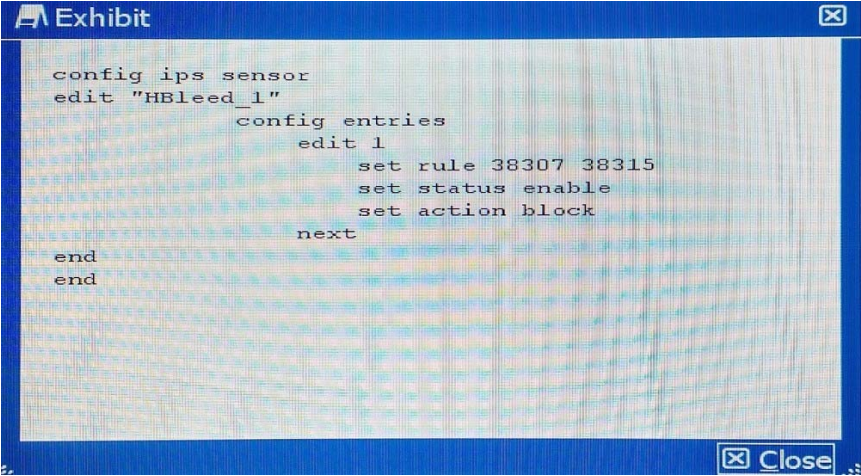
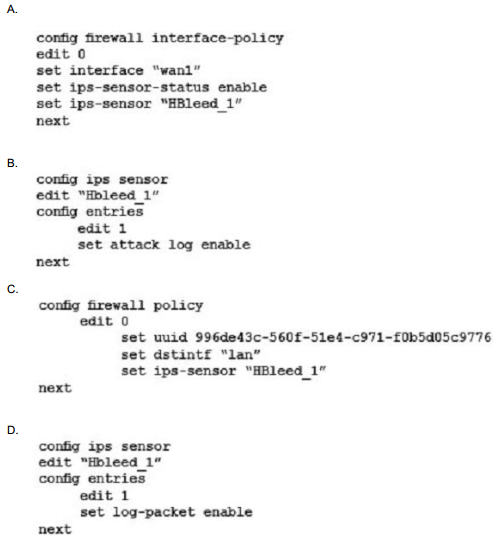
Correct Answer: B
QUESTION 8
Which command syntax would you use to configure the serial number of a FortiGate as its host name?
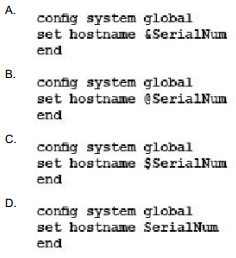
Correct Answer: C
QUESTION 9
Referring to the exhibit, which statement is true?
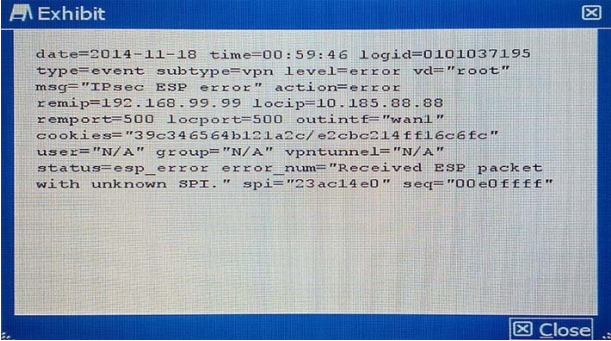
A. The packet failed the HMAC validation.
B. The packet did not match any of the local IPsec SAs.
C. The packet was protected with an unsupported encryption algorithm.
D. The IPsec negotiation failed because the SPI was unknown.
Correct Answer: A
QUESTION 10
You are asked to establish a VPN tunnel with a service provider using a third-party VPN device. The service provider has assigned subnet 30.30.30.0/24 for your outgoing traffic going towards the services hosted by the provider on network 20.20.20.0/24. You have multiple computers which will be accessing the remote services hosted by the service provider.
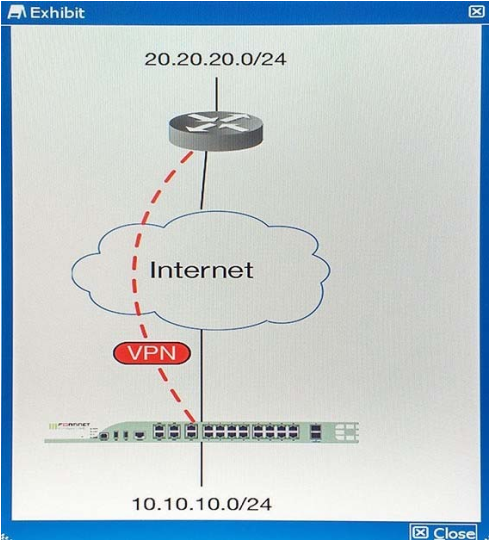
Which three configuration components meet these requirements? (Choose three.)
A. Configure an IP Pool of type Overload for range 30.30.30.10-30.30.30.10. Enable NAT on a policy from your LAN forwards the VPN tunnel and select that pool.
B. Configure IPsec phase 2 proxy IDs for a source of 10.10.10.0/24 and destination of 20.20.20.0/24.
C. Configure an IP Pool of Type One-to-One for range 30.30.30.10-30.30.30.10. Enable NAT on a policy from your LAN towards the VPN tunnel and select that pool.
D. Configure a static route towards the VPN tunnel for 20.20.20.0/24.
E. Configure IPsec phase 2 proxy IDs for a source of 30.30.30.0/24 and destination of 20.20.20.0/24.
Correct Answer: C
QUESTION 11
A university is looking for a solution with the following requirements:
– wired and wireless connectivity
– authentication (LDAP)
– Web filtering, DLP and application control
– data base integration using LDAP to provide access to those students who are up-to-date with their monthly payments
– support for an external captive portal
Which solution meets these requirements?
A. FortiGate for wireless controller and captive portal
FortiAP for wireless connectivity
FortiAuthenticator for user authentication and REST API for DB integration
FortiSwitch for PoE connectivity
FortiAnalyzer for log and report
B. FortiGate for wireless controller
FortiAP for wireless connectivity
FortiAuthenticator for user authentication, captive portal and REST API for DB integration FortiSwitch for PoE connectivity
FortiAnalyzer for log and report
C. FortiGate for wireless control and user authentication
FortiAuthenticator for captive portal and REST API for DB integration
FortiAP for wireless connectivity
FortiSwitch for PoE connectivity
FortiAnalyzer for log and report
D. FortiGate for wireless controller
FortiAP for wireless connectivity and captive portal
FortiSwitch for PoE connectivity
FortiAuthenticator for user authentication and REST API for DB integration
FortiAnalyzer for log and reports
Correct Answer: A
QUESTION 12
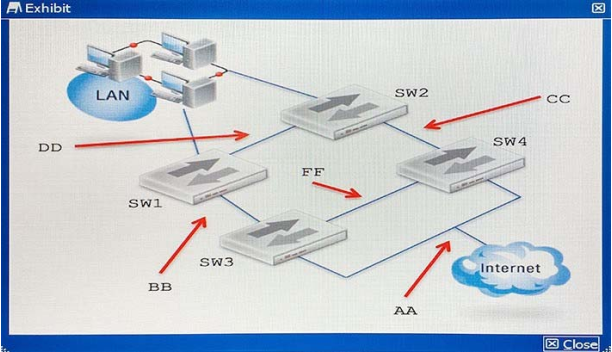
A customer wants to secure the network shown in the exhibit with a full redundancy design.
Which security design would you use?
A. Place a FortiGate FGCP Cluster between DD and AA, then connect it to SW1, SW2, SW3, and SW4.
B. Place a FortiGate FGCP Cluster between BB and CC, then connect it to SW1, SW2, SW3, and SW4.
C. Place a FortiGate FGCP Cluster between BB and AA, then connect it to SW1, SW2, SW3, and SW4.
D. Place a FortiGate FGCP Cluster between DD and FF, then connect it to SW1, SW2, SW3, and SW4.
Correct Answer: A
QUESTION 13
A customer has the following requirements:
– local peer with two Internet links
– remote peer with one Internet link
– secure traffic between the two peers
– granular control with Accept policies
Which solution provides security and redundancy for traffic between the two peers?
A. a fully redundant VPN with interface mode configuration
B. a partially redundant VPN with interface mode configuration
C. a partially redundant VPN with tunnel mode configuration
D. a fully redundant VPN with tunnel mode configuration
Correct Answer: B
QUESTION 14
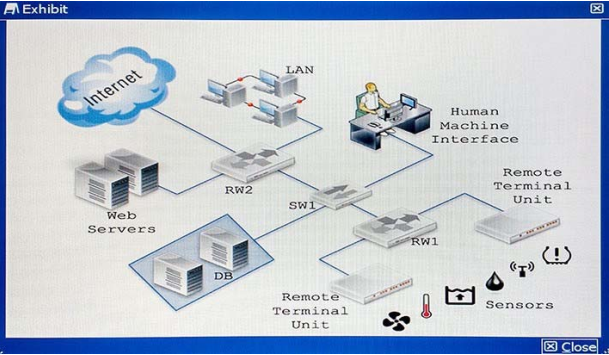
How would you apply security to the network shown in the exhibit?
A. Replace RW1 with a ruggedized FortiGate and RW2 with a normal FortiGate. Enable industrial category on the application control. Place a FortiGate to secure Web servers. Configure IPsec to secure sensors data. Place a ruggedized FortiAP to provide Wi-Fi to the sensors.
B. Replace RW1 with a normal FortiGate and RW2 with a ruggedized FortiGate. Enable industrial category on the application control. Place a FortiGate to secure Web servers. Configure IPsec to secure sensors data. Place a FortiAP to provide Wi-Fi to the sensors.
C. Replace RW1 with a normal FortiGate and RW2 with a ruggedized FortiGate. Enable industrial category on the Web filter. Place a FortiWeb to secure Web servers. Configure IPsec to secure sensors data. Place a ruggedized FortiAP to provide Wi-Fi to the sensors.
D. Replace RW1 with a normal FortiGate and RW2 with a ruggedized FortiGate. Enable industrial category on the application control. Place a FortiWeb to secure Web servers. Configure IPsec to secure sensors data. Place a ruggedized FortiAP to provide Wi-Fi to the sensors.
Correct Answer: D
QUESTION 15
Which command detects where a routing path is broken?
A. exec traceroute <destination>
B. exec route ping <destination>
C. diag route null
D. diag debug route <destination>
Correct Answer: A
QUESTION 16
Virtual Domains (VDOMs) allow a FortiGate administrator to do what?
A. Group two or more FortiGate units to form a single virtual device.
B. Split a physical FortiGate unit into multiple virtual devices.
C. Create multiple VLANs in a single physical interface,
D. Group multiple physical interfaces to form a single virtual interface.
Correct Answer: B
QUESTION 17
You notice that your FortiGate’s memory usage is very high and that the unit’s performance is adversely affected. You want to reduce memory usage. NSE8 dumps
Which three commands would meet this requirement? (Choose three.)


Correct Answer: ADE
QUESTION 18
The SECOPS team in your company has started a new project to store all logging data in a disaster recovery center. All FortiGates will log to a secondary FortiAnalyzer and establish a TCP session to send logs to the syslog server.
Which two configurations will achieve this goal? (Choose two.)
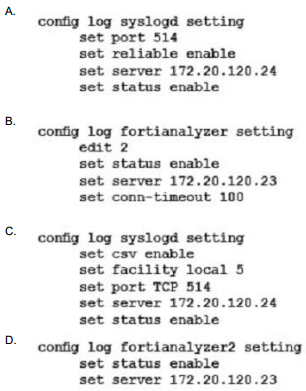
Correct Answer: AC
QUESTION 19
You want to enable traffic between 2001:db8:1::/64 and 2001:db8:2::/64 over the public IPv4 Internet.
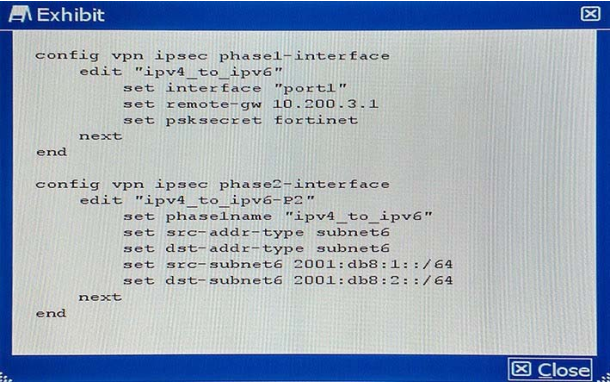
Given the CLI configuration shown in the exhibit, which two additional settings are required on this device to implement tunneling for the IPv6 transition? (Choose two.)
A. IPv4 firewall policies to allow traffic between the local and remote IPv6 subnets.
B. IPv6 static route to the destination phase2 destination subnet.
C. IPv4 static route to the destination phase2 destination subnet.
D. IPv6 firewall policies to allow traffic between the local and remote IPv6 subnets.
Correct Answer: D
QUESTION 20
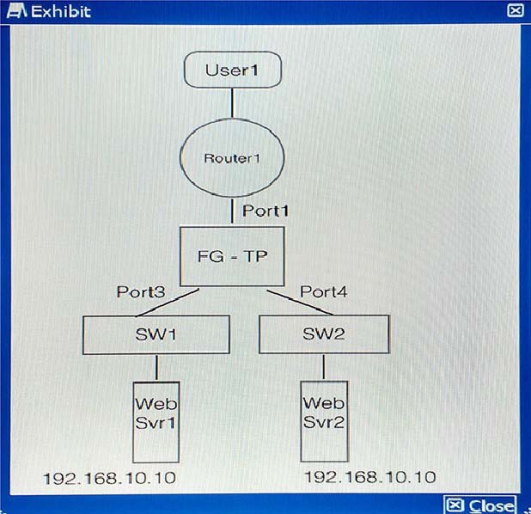
You have implemented FortiGate in transparent mode as shown in the exhibit. User1 from the Internet is trying to access the 192.168.10.10 Web servers.
Which two statements about this scenario are true? (Choose two.)
A. User1 would be able to access the Web server intermittently.
B. User1 would not be able to access any of the Web servers at all.
C. FortiGate learns Web servers MAC address when the Web servers transmit packets.
D. FortiGate always flood packets to both Web servers at the same time.
Correct Answer: AC
The best and most updated latest Fortinet NSE NSE8 dumps exam practice materials in PDF format free download from leads4pass. Helpful newest Fortinet NSE https://www.leads4pass.com/nse8.html dumps pdf training resources which are the best for clearing NSE8 exam test, and to get certified by Fortinet NSE. If you are looking to get Fortinet Network Security Expert 8 Written (800) certification by passing exam NSE8 then you can pass it in one go.
High quality Fortinet NSE NSE8 dumps vce youtube:
https://youtu.be/4eZnus416rY
Why Select Lead 4 pass?
leads4pass is the best provider of IT learning materials and the right choice for you to pass Fortinet NSE8 exam. Other brands started earlier, but the questions are not the newest and the price is relatively expensive. leads4pass provide the latest real and cheapest questions and answers, help you pass Fortinet NSE8 exam easily at first try.

Here Are Some Reviews From Our Customers:
You can click here to have a review about us: https://www.resellerratings.com/store/leads4pass
