The latest Symantec 250-428 dumps by leads4pass helps you pass the 250-428 exam for the first time! leads4pass
Latest Update Symantec 250-428 VCE Dump and 250-428 PDF Dumps, leads4pass 250-428 Exam Questions Updated, Answers corrected!
Get the latest leads4pass 250-428 dumps with Vce and PDF: https://www.leads4pass.com/250-428.html (Q&As: 165 dumps)
[Free 250-428 PDF] Latest Symantec 250-428 Dumps PDF collected by leads4pass Google Drive:
https://drive.google.com/file/d/1m_UsywykU9U97D5pEUnEiJwmwcntzgM7/
[leads4pass 250-428 Youtube] Symantec 250-428 Dumps can be viewed on Youtube shared by leads4pass
Latest Symantec 250-428 Exam Practice Questions and Answers
QUESTION 1
An organization identified a threat in their environment and needs to limit the spread of the threat. How should the SEP
Administrator block the threat using Application and Device Control?
A. Gather the MD5 hash of the file and create an Application Content Rule that blocks the file based on specific
arguments
B. Gather the MD5 hash of the file and create an Application Content Rule that blocks the file based on the file
fingerprint
C. Gather the MD5 hash of the file and create an Application Content Rule that uses regular expression matching
D. Gather the process name of the file and create an Application Content Rule that blocks the file based on the device id
type
Correct Answer: D
Reference: https://support.symantec.com/us/en/article.tech123745.html
QUESTION 2
A company receives a high number of reports from users that files being downloaded from internal web servers are
blocked. The Symantec Endpoint Protection administrator verifies that the Automatically trust any file downloaded from
an intranet website option is enabled.
Which configuration can cause Insight to block the files being downloaded from the internal web servers?
A. Intrusion Prevention is disabled.
B. Local intranet zone is configured incorrectly on the Windows clients browser settings.
C. Local intranet zone is configured incorrectly on the Mac client’s browser settings.
D. Virus and Spyware Definitions are out of date.
Correct Answer: B
QUESTION 3
Refer to the exhibit.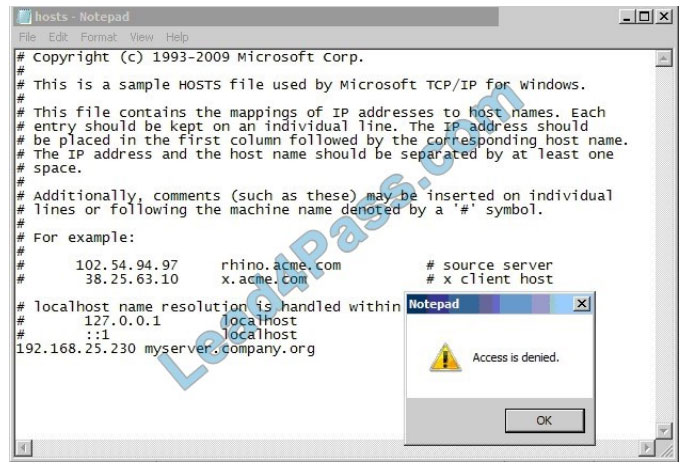
In the use case displayed in the exhibit.
Why is Notepad unable to save the changes to the file in the image below?
A. Tamper Protection is preventing Notepad from modifying the host file.
B. SONAR is set to block host file modifications.
C. System Lockdown is enabled.
D. SONAR High-Risk detection is set to Block.
Correct Answer: B
QUESTION 4
Solusell recently deployed SEP 14 in their environment and created the following groups for their computers: Desktops
Laptops Servers
What type of group structure does Solusell use?
A. Role
B. Combination
C. Folder
D. Geography
Correct Answer: C
Reference: https://support.symantec.com/us/en/article.tech134409.html
QUESTION 5
A company deploys Symantec Endpoint Protection (SEP) to 50 virtual machines running on a single ESXi host.
Which configuration change can the administrator make to minimize sudden IOPS impact on the ESXi server while each SEP endpoint communicates with the Symantec Endpoint Protection Manager?
A. increase Download Insight sensitivity level
B. reduce the heartbeat interval
C. increase download randomization window
D. reduce the number of content revisions to keep
Correct Answer: C
QUESTION 6
An organization has a group of 500 SEP for Windows Clients running 12.1 RU5. The organization wants to migrate the
clients to 14 RU1 but must minimize WAN bandwidth usage. What installation method should the organization use?
A. Push Deployment Wizard
B. Clients Install-Package hosted on a local HTTP Server
C. Client Deployment Wizard
D. Auto Upgrade
Correct Answer: D
QUESTION 7
An administrator is recovering from a Symantec Endpoint Manager (SEPM) site failure.
Which file should the administrator use during an install of SEPM to recover the lost environment according to Symantec
Disaster Recovery Best Practice documentation?
A. original installation log
B. recovery_timestamp file
C. settings. properties file
D. Sylink.xml file from the SEPM
Correct Answer: B
References: https://support.symantec.com/en_US/article.TECH160736.html
QUESTION 8
A threat was detected by Auto-Protect on a client system.
Which command can an administrator run to determine whether additional threats exist?
A. Restart Client Computer
B. Update Content and Scan
C. Enable Network Threat Protection
D. Enable Download Insight
Correct Answer: A
QUESTION 9
An administrator is unknowingly trying to connect to a malicious website and download a known threat within a .rar file.
All Symantec Endpoint Protection technologies are installed on the client\\’s system. Drag and drop the technologies to
the right side of the screen in the sequence necessary to block or detect the malicious file.
Select and Place: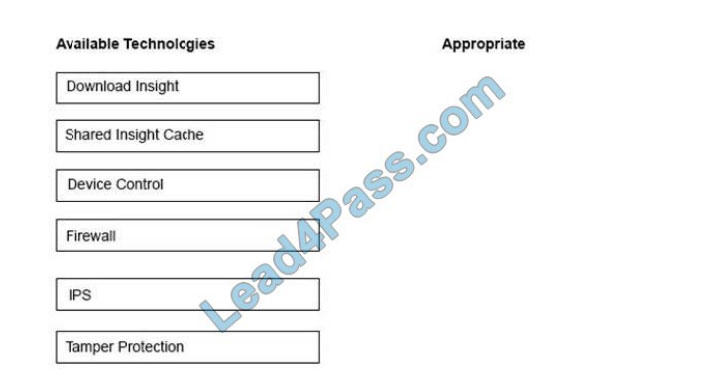
Correct Answer:
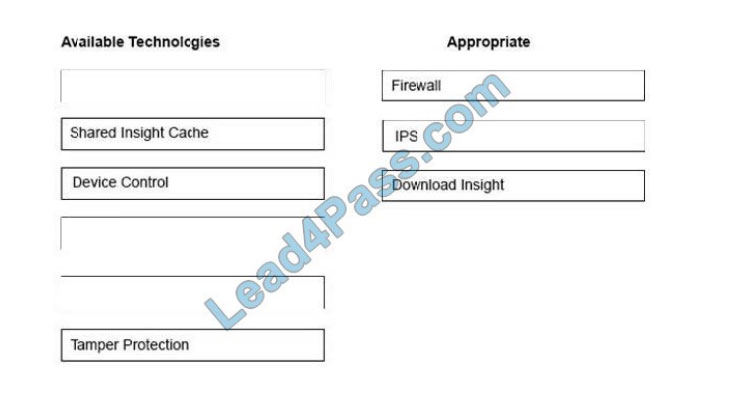
QUESTION 10
What steps should an administrator take to utilize Symantec Endpoint Protection in a non-persistent virtual desktop
infrastructure?
A. Setup the base image and configure client logs in the SEPM console
B. Setup the base image and configure a separate purge interval for offline non-persistent VDI clients in the SEPM
console
C. Setup the base image and delete offline clients in the SEPM console
D. Setup the base image and configure the “Delete clients that have not connected for a specified time” setting from the default of 30 to 1 in the SEPM console
Correct Answer: B
Reference: https://support.symantec.com/us/en/article.HOWTO81120.html#v74771361
QUESTION 11
Which policy should an administrator modify to enable Virtual Image Exception (VIE) functionality?
A. Host Integrity Policy
B. Virus and Spyware Protection Policy
C. Exceptions Policy
D. Application and Device Control Policy
Correct Answer: B
References: https://www.symantec.com/connect/articles/sep-121-virtualization
QUESTION 12
An organization created a rule in the Application and Device Control policy to block peer-to-peer applications. What two
other protection technologies can block and log such unauthorized applications? (Choose two.)
A. Memory Exploit Mitigation
B. Virus and Spyware Protection
C. Custom IPS Signatures
D. Host Integrity
E. Firewall
Correct Answer: CE
Reference: https://support.symantec.com/us/en/article.tech122597.html
QUESTION 13
Which object in the Symantec Endpoint Protection Manager console describes the most granular level to which a policy
can be assigned?
A. Group
B. Computer
C. User
D. Client
Correct Answer: A
latest updated Symantec 250-428 exam questions from the leads4pass 250-428 dumps! 100% pass the 250-428 exam!
Download leads4pass 250-428 VCE and PDF dumps: https://www.leads4pass.com/250-428.html (Q&As: 165 dumps)
Get free Symantec 250-428 dumps PDF online: https://drive.google.com/file/d/1m_UsywykU9U97D5pEUnEiJwmwcntzgM7/