Share CheckPoint 156-915.80 exam practice questions and answers from leads4pass latest updated 156-915.80 dumps free of charge.
Get the latest uploaded 156-915.80 dumps pdf from google driver online. To get the full CheckPoint 156-915.80 dumps PDF or dumps
VCE visit: https://www.leads4pass.com/156-915-80.html (Q&As: 466). all CheckPoint 156-915.80 exam questions have been updated, the answer has been corrected!
Make sure your exam questions are real and effective to help you pass your first exam!
[CheckPoint 156-915.80 Dumps pdf] Latest CheckPoint 156-915.80 Dumps PDF collected by leads4pass Google Drive:
https://drive.google.com/file/d/1wWuI9Xt8L7ippiCkeQoa_0pEeuU80h5j/
[CheckPoint 156-915.80 Youtube] CheckPoint 156-915.80 exam questions and answers are shared free of charge from Youtube watching uploads from leads4pass
Latest Update CheckPoint 156-915.80 Exam Practice Questions and Answers Online Test
QUESTION 1
You want to implement Static Destination NAT in order to provide external, Internet users access to an internal Web
Server that has a reserved (RFC 1918) IP address. You have an unused valid IP address on the network between your
Security Gateway and ISP router. You control the router that sits between the firewall external interface and the
Internet.
What is an alternative configuration if proxy ARP cannot be used on your Security Gateway?
A. Publish a proxy ARP entry on the ISP router instead of the firewall for the valid IP address.
B. Place a static ARP entry on the ISP router for the valid IP address to the firewall\\’s external address.
C. Publish a proxy ARP entry on the internal Web server instead of the firewall for the valid IP address.
D. Place a static host route on the firewall for the valid IP address to the internal Web server.
Correct Answer: B
QUESTION 2
Which of these options is an implicit MEP option?
A. Primary-backup
B. Source address based
C. Round robin
D. Load Sharing
Correct Answer: A
There are three methods to implement implicit MEP:
First to Respond, in which the first Security Gateway to reply to the peer Security Gateway is chosen. An organization
would choose this option if, for example, the organization has two Security Gateways in a MEP configuration – one in
London, the other in New York. It makes sense for VPN-1 peers located in England to try the London Security Gateway
first and the NY Security Gateway second. Being geographically closer to VPN peers in England, the London Security
Gateway is the first to respond, and becomes the entry point to the internal network. See: First to Respond.
Primary-Backup, in which one or multiple backup Security Gateways provide “high availability” for a primary Security
Gateway. The remote peer is configured to work with the primary Security Gateway, but switches to the backup
Security
Gateway if the primary goes down. An organization might decide to use this configuration if it has two machines in a
MEP environment, one of which is stronger than the other. It makes sense to configure the stronger machine as the
primary.
Or perhaps both machines are the same in terms of strength of performance, but one has a cheaper or faster
connection to the Internet. In this case, the machine with the better Internet connection should be configured as the
primary. See:
Primary-Backup Security Gateways.
Load Distribution, in which the remote VPN peer randomly selects a Security Gateway with which to open a connection.
For each IP source/destination address pair, a new Security Gateway is randomly selected. An organization might have
a
number of machines with equal performance abilities. In this case, it makes sense to enable load distribution. The
machines are used in a random and equal way. See: Random Selection.
Reference: https://sc1.checkpoint.com/documents/R77/CP_R77_VPN_AdminGuide/13812.htm
QUESTION 3
You have a Gateway is running with 2 cores. You plan to add a second gateway to build a cluster and used a device
with 4 cores. How many cores can be used in a Cluster for Firewall-kernel on the new device?
A. 3
B. 2
C. 1
D. 4
Correct Answer: D
QUESTION 4
Which of the following process pulls are applications monitoring status?
A. fwd
B. fwm
C. cpwd
D. cpd
Correct Answer: C
Reference: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=andsolutionid=sk97638
QUESTION 5
Jack is using SmartEvent and does not see the identities of the users on the events. As an administrator with full
access, what does he need to do to fix his issue?
A. Open SmartDashboard and toggle the Show or Hide Identities Icon, then re-open SmartEvent
B. Open SmartEvent, Click on Query Properties, and select the User column
C. Open SmartEvent, go to the Policy Tab, select General Settings from the left column > User Identities and check the
box Show Identities
D. Open SmartEvent and toggle the Show or Hide Identities icon
Correct Answer: C
QUESTION 6
Joey and Vanessa are firewall administrators in their company. Joey wants to run the Management API server on his
Security Management Server. He is logging in to a Smart Console and goes to the Manage and Settings > Blade. In
Management
API section, he proceeds to Advanced Settings. He likes to set up the Management API server to automatically run at
startup. He is surprised because this functionality is already selected by default.
What is the reason, that functionality is already enabled?
A. Joey is an administrator of Distributed Security Management with at least 4GB of RAM.
B. Vanessa is an administrator of Standalone Security Management with at least 6GB of RAM.
C. Vanessa already enabled this feature on the Security server before him, but didn\\’t tell Joey.
D. Joey is an administrator of StandAlone Security Management with Gateway with 6GB of RAM.
Correct Answer: A
Reference: https://sc1.checkpoint.com/documents/R80/CP_R80_SecMGMT/html_frameset.htm?topic=documents/R80/CP_R80_SecMGMT/117948
QUESTION 7
How could you compare the Fingerprint shown to the Fingerprint on the server? Exhibit: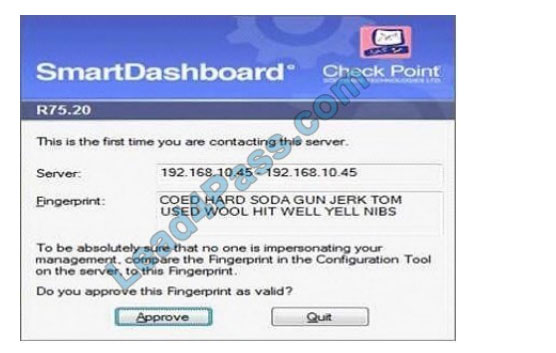
A. Run cpconfig, select the Certificate\\’s Fingerprint option, and view the fingerprint
B. Run cpconfig, select the GUI Clients option, and view the fingerprint
C. Run cpconfig, select the Certificate Authority option, and view the fingerprint
D. Run sysconfig, select the Server Fingerprint option, and view the fingerprint
Correct Answer: A
QUESTION 8
Where do you verify that UserDirectory is enabled?
A. Verify that Security Gateway > General Properties > Authentication > Use UserDirectory (LDAP) for Security
Gateways are checked
B. Verify that Global Properties > Authentication > Use UserDirectory (LDAP) for Security Gateways is checked
C. Verify that Security Gateway > General Properties > UserDirectory (LDAP) > Use UserDirectory (LDAP) for Security
Gateways are checked
D. Verify that Global Properties > UserDirectory (LDAP) > Use UserDirectory (LDAP) for Security Gateways is checked
Correct Answer: D
QUESTION 9
How do you recover communications between your Security Management Server and Security Gateway if you lock
yourself out through a rule or policy mis-configuration?
A. fw unload policy
B. fw unloadlocal
C. fw delete all.all@localhost
D. fwm unloadlocal
Correct Answer: B
QUESTION 10
Paul has just joined the MegaCorp security administration team. Natalie, the administrator, creates a new administrator
account for Paul in SmartDashboard and installs the policy. When Paul tries to login it fails. How can Natalie verify
whether Paul\\’s IP address is predefined on the security management server?
A. Login to Smart Dashboard, access Properties of the SMS, and verify whether Paul\\’s IP address is listed.
B. Type cpconfig on the Management Server and select the option “GUI client List” to see if Paul\\’s IP address is listed.
C. Login into Smart Dashboard, access Global Properties, and select Security Management, to verify whether Paul\\’s IP address is listed.
D. Access the WEBUI on the Security Gateway and verify whether Paul\\’s IP address is listed as a GUI client.
Correct Answer: B
QUESTION 11
SandBlast agent extends 0-day prevention to what part of the network?
A. Web Browsers and user devices
B. DMZ server
C. Cloud
D. Email servers
Correct Answer: A
QUESTION 12
Selecting an event displays its configurable properties in the Detail pane and a description of the event in the
Description of the pane. Which is NOT an option to adjust or configure?
A. Severity
B. Automatic reactions
C. Policy
D. Threshold
Correct Answer: C
Reference: https://sc1.checkpoint.com/documents/R76/CP_R76_SmartEvent_AdminGuide/17401.htm
QUESTION 13
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP
addresses to minimize malware infection and unauthorized access risks. Thus, the gateway policy permits access only
from John\\’s desktop which is assigned an IP address 10.0.0.19 via DHCP.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department
gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains
a rule that lets John Adams access the HR Web Server from his laptop. He wants to move around the organization and
continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any
machine and from any location. John plugged in his laptop to the network on a different network segment and he is not
able to connect. How does he solve this problem?
A. John should install the Identity Awareness Agent
B. The firewall admin should install the Security Policy
C. John should lock and unlock the computer
D. Investigate this as a network connectivity issue
Correct Answer: B
For the full CheckPoint 156-915.80 exam dumps from leads4pass 156-915.80 Dumps pdf or Dumps VCE visit: https://www.leads4pass.com/156-915-80.html (Q&As: 466 dumps)
ps.
Get free CheckPoint 156-915.80 dumps PDF online: https://drive.google.com/file/d/1wWuI9Xt8L7ippiCkeQoa_0pEeuU80h5j/