Are you ready for Cisco 210-260 exam test? Prepare for Cisco 210-260 exam test with latest Cisco CCNA Security 210-260 dumps pdf practice files and vce youtube demo update free shared. Newest Cisco CCNA Security 210-260 dumps exam questions and answers free download from leads4pass. “Implementing Cisco Network Security” is the name of Cisco CCNA Security https://www.leads4pass.com/210-260.html exam dumps which covers all the knowledge points of the real Cisco exam. The best useful Cisco CCNA Security 210-260 dumps pdf training materials and study guides free update, pass Cisco 210-260 exam test easily at first try.
Latest Cisco 210-260 dumps pdf practice files: https://drive.google.com/open?id=0B_7qiYkH83VRcnI0SE83bHBvQ1k
Latest Cisco 210-060 dumps pdf practice files: https://drive.google.com/open?id=0B_7qiYkH83VRSHJTTV9NMjQ0dmc
QUESTION 1
How can you detect a false negative on an IPS?
A. View the alert on the IPS.
B. Review the IPS log.
C. Review the IPS console.
D. Use a third-party system to perform penetration testing.
E. Use a third-party to audit the next-generation firewall rules.
Correct Answer: D
QUESTION 2
How can FirePOWER block malicious email attachments?
A. It forwards email requests to an external signature engine.
B. It scans inbound email messages for known bad URLs.
C. It sends the traffic through a file policy.
D. It sends an alert to the administrator to verify suspicious email messages.
Correct Answer: C
QUESTION 3
Which tool can an attacker use to attempt a DDoS attack?
A. botnet
B. Trojan horse
C. virus
D. adware
Correct Answer: A
QUESTION 4
Which two statements about stateless firewalls are true? (Choose two.)
A. They compare the 5-tuple of each incoming packet against configurable rules.
B. They cannot track connections.
C. They are designed to work most efficiently with stateless protocols such as HTTP or HTTPS.
D. Cisco IOS cannot implement them because the platform is stateful by nature.
E. The Cisco ASA is implicitly stateless because it blocks all traffic by default.
Correct Answer: AB
QUESTION 5
Which three ESP fields can be encrypted during transmission? 210-260 dumps (Choose three.)
A. Security Parameter Index
B. Sequence Number
C. MAC Address
D. Padding
E. Pad Length
F. Next Header
Correct Answer: DEF
QUESTION 6
In the router ospf 200 command, what does the value 200 stand for?
A. process ID
B. area ID
C. administrative distance value
D. ABR ID
Correct Answer: A
QUESTION 7
Refer to the exhibit.

Which statement about the given configuration is true?
A. The single-connection command causes the device to establish one connection for all TACACS transactions.
B. The single-connection command causes the device to process one TACACS request and then move to the next server.
C. The timeout command causes the device to move to the next server after 20 seconds of TACACS inactivity.
D. The router communicates with the NAS on the default port, TCP 1645.
Correct Answer: A
QUESTION 8
What is example of social engineering
A. Gaining access to a building through an unlocked door.
B. something about inserting a random flash drive.
C. gaining access to server room by posing as IT
D. Watching other user put in username and password (something around there)
Correct Answer: C
QUESTION 9
In which three ways does the TACACS protocol differ from RADIUS? (Choose three.)
A. TACACS uses TCP to communicate with the NAS.
B. TACACS can encrypt the entire packet that is sent to the NAS.
C. TACACS supports per-command authorization.
D. TACACS authenticates and authorizes simultaneously, causing fewer packets to be transmitted.
E. TACACS uses UDP to communicate with the NAS.
F. TACACS encrypts only the password field in an authentication packet.
Correct Answer: ABC
QUESTION 10
What can the SMTP preprocessor in FirePOWER normalize?
A. It can extract and decode email attachments in client to server traffic.
B. It can look up the email sender.
C. It compares known threats to the email sender.
D. It can forward the SMTP traffic to an email filter server.
E. It uses the Traffic Anomaly Detector.
Correct Answer: A
QUESTION 11
Which option is the most effective placement of an IPS device within the infrastructure? 210-260 dumps
A. Inline, behind the internet router and firewall
B. Inline, before the internet router and firewall
C. Promiscuously, after the Internet router and before the firewall
D. Promiscuously, before the Internet router and the firewall
Correct Answer: A
QUESTION 12
Which two authentication types does OSPF support? (Choose two.)
A. plaintext
B. MD5
C. HMAC
D. AES 256
E. SHA-1
F. DES
Correct Answer: AB
QUESTION 13
Which of the following pairs of statements is true in terms of configuring MD authentication?
A. Interface statements (OSPF, EIGRP) must be configured; use of key chain in OSPF
B. Router process (OSPF, EIGRP) must be configured; key chain in EIGRP
C. Router process (only for OSPF) must be configured; key chain in EIGRP
D. Router process (only for OSPF) must be configured; key chain in OSPF
Correct Answer: C
QUESTION 14
What feature defines a campus area network?
A. It has a single geographic location.
B. It has limited or restricted Internet access.
C. It has a limited number of segments.
D. it lacks external connectivity.
Correct Answer: A
QUESTION 15
which term best describes the concept of preventing the modification of data in transit and in storage?
A. Confidentiality
B. Integrity
C. Availability
D. fidelity
Correct Answer: B
QUESTION 16
In what type of attack does an attacker virtually change a device\’s burned-in address in an attempt to circumvent access lists and mask the device\’s true identity?
A. gratuitous ARP
B. ARP poisoning
C. IP spoofing
D. MAC spoofing
Correct Answer: D
QUESTION 17
Refer to the exhibit.
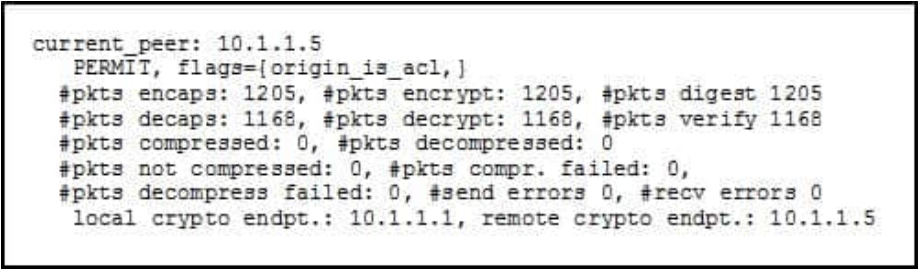
While troubleshooting site-to-site VPN, you issued the show crypto ipsec sa command. 210-260 dumps What does the given output show?
A. IPSec Phase 2 is established between 10.1.1.1 and 10.1.1.5.
B. ISAKMP security associations are established between 10.1.1.5 and 10.1.1.1.
C. IKE version 2 security associations are established between 10.1.1.1 and 10.1.1.5.
D. IPSec Phase 2 is down due to a mismatch between encrypted and decrypted packets.
Correct Answer: A
QUESTION 18
Which statement correctly describes the function of a private VLAN?
A. A private VLAN partitions the Layer 2 broadcast domain of a VLAN into subdomains
B. A private VLAN partitions the Layer 3 broadcast domain of a VLAN into subdomains
C. A private VLAN enables the creation of multiple VLANs using one broadcast domain
D. A private VLAN combines the Layer 2 broadcast domains of many VLANs into one major broadcast domain
Correct Answer: A
QUESTION 19
What are two ways to prevent eavesdropping when you perform device-management tasks? (Choose two.)
A. Use an SSH connection.
B. Use SNMPv3.
C. Use out-of-band management.
D. Use SNMPv2.
E. Use in-band management.
Correct Answer: AB
QUESTION 20
Which firewall configuration must you perform to allow traffic to flow in both directions between two zones?
A. You must configure two zone pairs, one for each direction.
B. You can configure a single zone pair that allows bidirectional traffic flows for any zone.
C. You can configure a single zone pair that allows bidirectional traffic flows for any zone except the self zone.
D. You can configure a single zone pair that allows bidirectional traffic flows only if the source zone is the less secure zone.
Correct Answer: A
The best and most updated latest Cisco CCNA Security 210-260 dumps exam practice materials in PDF format free download from leads4pass. High quality Cisco CCNA Security https://www.leads4pass.com/210-260.html dumps pdf training resources which are the best for clearing 210-260 exam test, and to get certified by Cisco CCNA Security, download one of the many PDF readers that are available for free.
High quality Cisco CCNA Security 210-260 dumps vce youtube: https://youtu.be/seDmEyXcd3w